
- Interceptor Ng For Mac Catalina
- Intercepter Ng Github
- Interceptor Ng For Mac Os
- Interceptor Ng For Mac Installer
- Intercepter Ng Mac Os
- Intercepter Ng Apk
Hi fellas! Lately i released a new version of Intercepter-NG for Android and today i want to discuss one of it's features.
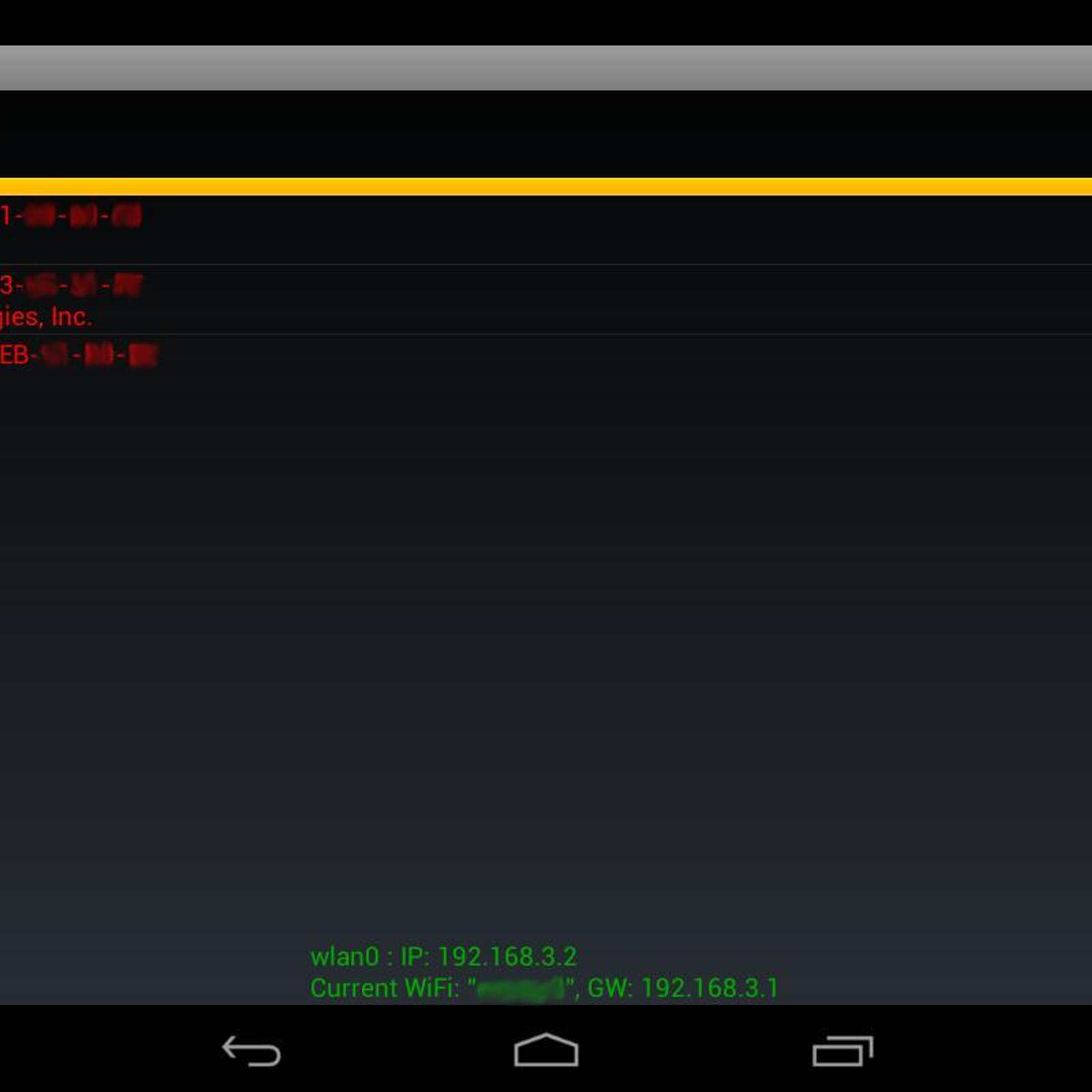
For years, even in original Windows version, Intercepter has used a simple method to detect and distinguish one OS from another. First, it checked the value of TTL by sending ICMP requests and whether there was at least one open TCP port it checked both TTL + TCP Window Size.
That way i was able to get these results:
While the developer is fixing the problem, try using an older version. If you need the previous version of Intercepter-NG, check out the app's version history which includes all versions available to download. Download prior versions of Intercepter-NG for Android. All previous versions of Intercepter-NG are virus-free and free to download at. Exploit prevention stops the techniques used in file-less, malware-less, and exploit-based attacks. While there are millions of pieces of malware in existence, and thousands of software vulnerabilities waiting to be exploited, there are only handful of exploit techniques attackers rely on as part of the attack chain – and by taking away the key tools hackers love to use, Intercept X stops. Intercepter-NG is a multifunctional network toolkit for various types of IT specialists. The main purpose is to recover.interesting. data from the network stream and perform different kinds of MiTM attacks. Intercepter-NG offers the following features: + Sniffing passwordshashes of the types. Free Download Intercepter-NG APK For PC Windows 7/8/8.1/10/XP Free Download Intercepter-NG APK For PC:Our site helps you to install android apps/games available on Google Play Store. Intercepter-NG For Android Reviews. It is called auditing networks when in reality it is more about stealing passwords. But hey we are going to assume that in your case you want to legitimately check how safe your WiFi connection is and whether there are any intruders connected in order to block them.
- Linux 2.4.x2.6.x
- Linux 3.xAndroid
- FreeBSDMacOS X
- FreeBSD
- OpenBSD
- HP-UX
- Windows 2000XP SP2
- Windows XP
- Windows 2003
- Windows 7810
- Cisco IOS
- Solaris
Although this list is extremely short, it's better than nothing...
What comes to your mind when you hear 'OS detection'? Right, nmap...but it means that you need to be able to connect to the host you are interested in and spend some time analyzing it.
What if you only have a network capture? Passive OS fingerprinting you'd say...yes, we have Satori and p0f.
Satori and it's database is the only 'up to date' tool and i decided to include it in Intercepter, but the problem arose shortly after i looked deeper on it. It contains many identical TCP fingerprints for different systems - which is good and useful in general. But somehow i have to pick only one result and print it during the network scan.

Satori, p0f and other passive OS fingerprinting tools were intended to work with captures or live traffic from any kind of network, so MAC address was never considered.
In my case, Intercepter works only in ethernet area with direct access to a network devices with unique MAC addresses.
Now, the main idea is to add the first 3 bytes of a known device's MAC to it's TCP SYNACK fingerprint and voila! a common linux fingerprint turns into something unique:
C8D3A3;5792:64:1:60:M1460,S,T,N,W1:ZAT=Linux 2.4 ; D-Link DSL-2740U
F81A67;5792:64:1:60:M1460,S,T,N,W1:ZAT=Linux 2.6 ; TP-Link WR842ND
CC5D4E;5792:64:1:60:M1460,S,T,N,W1:ZAT=Linux 2.6 ; ZYXEL Keenetic Giga
8CEA1B;5792:64:1:60:M1460,S,T,N,W1:ZAT=Edge-Core ECS2100 ; Switch
Or a common fingerprint for Android turns into:
F8C39E;65535:64:1:60:M1460,S,T,N,W8:ZAT=Android 9 ; Honor 9 Lite
2047DA;65535:64:1:60:M1460,S,T,N,W8:ZAT=Android 9 ; Xiaomi Redmi Note 5
08CC27;65535:64:1:60:M1460,S,T,N,W8:ZAT=Android 9 ; Motorola E6 Plus
8C3AE3;65535:64:1:60:M1460,S,T,N,W8:ZAT=Android 5 ; LG G2
That way we are able to detect the exact model of a device! Using fingerprints of that type Intercepter can detect a lot of devices just in a few seconds. All we need is to collect as many fingerprints as possible. I didn't want to create a new format, that's why i picked the one from Satori, it's nice and clear, and so, with minor changes the database of Intercepter is suitable for Satori too. There are also generic fingerprints such as:
000000;8192:128:1:60:M1460,N,W8,S,T:AT=Windows 7 / 8 / 2008 / 2012 / 2016 ;
or
000000;65535:64:1:60:M1460,S,T,N,W8:ZAT=Android 5-10+ ;
Intercepter uses them in case it hasn't found the exact value by MAC.
1. Built-in button in Android version of Intercepter.
It generates the fingerprint of your own device. Just make sure MAC randomization is turned off.
2. New X-Scan mode shows the fingerprint of a remote device. It needs at least one open TCP port.
3. All unknown fingerprints appear during the network scan as extra info.
Interceptor Ng For Mac Catalina

4. I've updated the original Intercepter-NG to 1.0+ version. It shows fingerprints for every device on the network - much easier to collect a lot of records.
You've seen some examples above, so if you want to help me, collect fingerprints and set the 'OS version' andor 'Device model' and mail them to me - intercepter.mail@gmail.com.
For common computers and notebooks only OS information is interesting.
Your help will be useful not only for Intercepter or Satori, but for the other tools such as NetworkMiner. Contribute or die!
Intercepter Ng Github
Current version of database is published here - https://github.com/intercepter-ng/intercepter-ng.github.io/blob/master/intercepter_fingerprints_database.txt
Site: sniff.su

Mirror: https://github.com/intercepter-ng/intercepter-ng.github.io
Twitter: twitter.com/IntercepterNG
Blog: intercepter-ng.blogspot.ru
Satori: https://github.com/xnih/satori
Changelog for 2.6:
+ Automatical Save&Restore of routing rules and iptables
+ Preloaded results of the last scan + prescan on startup
+ Text resize by gestures, tab switch by swipes, vibro reactions
+ Port Scan upgraded to X-Scan with EternalBlue checker
+ HSTS Spoofing with improved sslstrip
+ LOTS of other fixes and improvements
Interceptor Ng For Mac Os
* UI updated
* No more SuperSU and Busybox dependencies -> Magisk
Interceptor Ng For Mac Installer
* Android support from 4.4 up to 10+ (x86, ARM, ARMv8)
Intercepter Ng Mac Os
Intercepter Ng Apk
We all can be part of the solution. Digital downloads are the 'green' answer to demanding fewer resources for your computer's needs. What you get is software with an environmental footprint of zero while still staying up-to-date.
Digital downloads are one part of the larger trend in making our lives - both professional and personal - cleaner, more efficient, and better. Continue reading to see what else you can do to improve your green computing.
Limit screen-saver use. A screen saver does not save energy. In fact, more often than not, a screen saver not only will draw power for the monitor, but also will keep the CPU from shutting down. Instead, set your computer to turn off the monitor first, then go into standby mode after a longer period of inactivity.
Disconnect your Virtual Private Network (VPN) when not actively using your corporate network. Being connected may limit your system's ability to enter standby mode.
Many popular computer games and other third party software packages that run in the background will not allow the computer to go to sleep - even if they are paused or the active window is minimized.
Some web sites or pages that have active banners and or animated advertisements will not allow the computer to sleep on its own and must be closed, or the computer put manually into a sleep state.
Enabled power management to place your monitor, hard drives and computer into a low-power 'sleep' mode after a period of inactivity.
Monitor/display sleep: Turn off after 15 minutes or less
Turn off hard drives/hard disk sleep: 15 minutes or less
System standby/sleep: After 30 minutes or less
Advanced users may wish to establish multiple power schemes to address different usage models. For example, you can create a power scheme for playing music CDs that shuts off your hard drive and monitor immediately, but never puts your system into standby mode.
To further reduce power consumption, turn off computing and peripheral devices that are not being used or being used for an extended period of time such as overnight.
Plug all your electronics into one surge protector, so you can easily switch them all off when you leave the room or go to sleep. Most power supplies (such as your cell phone charger) continue to draw power and generate heat even when not attached to a device.






